Secure Shell (SSH) is a widely used protocol to access Linux servers remotely. By default, SSH uses port 22 for connection. Using the default ssh port poses some security risks.
As SSH is widely used, and SSH port 22 is known to everybody often attacker target servers to conduct brute-force attacks using default port 22. If attackers gain access to your server, they may access sensitive information and cause a broken system. So, instead of leaving the default ssh port to the internet, you can change it to a custom port which increases security significantly.
In this blog post, I’ll show step-by-step how to change the default SSH port and secure your server.
Table of Contents
Change Default SSH Port
Throughout history, many cyber attacks have been launched. For example, In 2017, a group of hackers exploited a vulnerability in Microsoft Windows with wannacry virus. The ransomware spread around the world very rapidly. They spread the malware with the help of the server by scanning the server with default port 22.
Using a non-standard SSH port enhances your server security. You can choose your non-standard port freely, but there are some limitations. For various services and applications, some ports are reserved, and selecting a reserved port results broken system or lost access to the server.
You should avoid this list of reserved ports when choosing a custom port for your SSH server.
| Port Number | Protocol | Service/Application |
|---|---|---|
| 20 | TCP | FTP Data |
| 21 | TCP | FTP Control |
| 22 | TCP/UDP | SSH |
| 23 | TCP | Telnet |
| 25 | TCP | SMTP |
| 53 | TCP/UDP | DNS |
| 80 | TCP | HTTP |
| 110 | TCP | POP3 |
| 119 | TCP | NNTP |
| 123 | UDP | NTP |
| 143 | TCP | IMAP |
| 161 | UDP | SNMP |
| 194 | TCP | IRC |
| 443 | TCP | HTTPS |
| 465 | TCP | SMTPS |
| 587 | TCP | SMTP (Message Submission) |
| 993 | TCP | IMAPS |
| 995 | TCP | POP3S |
| 1433 | TCP | Microsoft SQL Server |
| 3306 | TCP | MySQL |
| 3389 | TCP | Remote Desktop Protocol |
| 5432 | TCP | PostgreSQL |
Please note that this is not a complete list. Other ports may be open depending on the application or service you use. Please check the ports associated with your application and don’t use them as SSH ports.
Step 1: Connect to your Server
To change your default SSH port, you need to connect to your server first. If you use macOS or Linux, you can connect your server using the following command.
ssh user@host_ip_addressIf you use the Windows Operating system, you can use PuTTY to connect to your server. You can also use Powershell to connect to the server. After establishing the connection, log in to a user account with root privilege.
Step 2: Edit the SSH Configuration File
You need to edit your server’s SSH configuration file to specify a new port number. Server SSH configuration is located /etc/ssh/sshd_config on most Linux servers. You can open the configuration file with your favorite text editor. To open the configuration file in the nano editor, enter the following command in the terminal.
sudo nano /etc/ssh/sshd_configStep 3: Change the SSH Port Number
In the configuration file location of the line where the port number is specified.
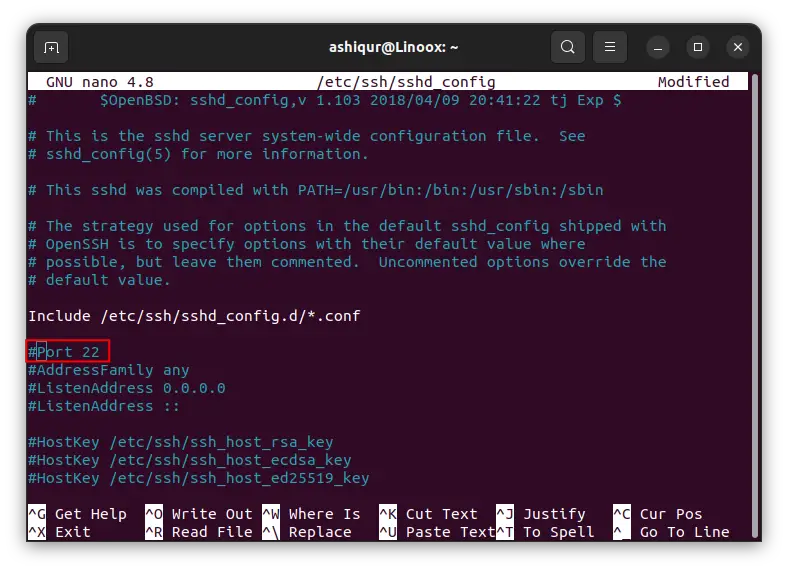
Once you find the line, uncomment the line by removing the ‘#’ symbol and changing the port number to a non-standard SSH port.
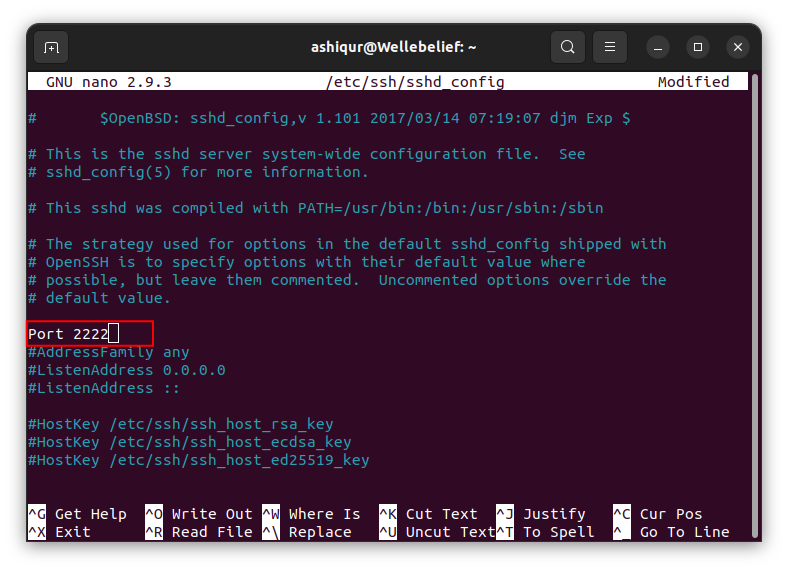
After changing the port, save the file and exit the editor. If you use nano editor, use CTRL + O to write the file and CTRL + X to exit the editor.
Don’t close the connection before adding firewall rule otherwise you can’t access to the server
Step 4: Configure Your Firewall to accept new port
The newly added port is inactive and will be blocked by the server firewall. To use the new SSH port, you must create a firewall rule specifying the new port as an SSH port.
1. For Debian/Ubuntu System
Before adding a firewall rule, check whether your firewall is active. To check the firewall status, use the following command.
sudo ufw statusIf your firewall is inactive, you need to activate it before adding a new rule. To activate the firewall, use the following command.
sudo ufw enableOnce your firewall is enabled, add a new rule to open the newly created port for connection. To create new firewall rules, use the following command.
sudo ufw allow 2222/tcpAfter setting the rule to the firewall, you need to reload the firewall to take effect. To reload the firewall use
sudo ufw reload2. For RHEL/CentOS System
To check whether the firewall is running or not, use the following command
sudo firewall-cmd --stateIf the system uses iptables, use this command
sudo iptables -LIf the firewall is not running, you can enable the firewall by using the following command.
sudo systemctl enable firewalldFor iptables, use the following command.
sudo systemctl enable iptablesIf the system uses firewall, you can use this command to add firewall rule to accept a new SSH port for SSH connection.
sudo firewall-cmd --add-port=2222/tcp --permanentOr, if the system is using iptables, you can use this command to add a firewall rule for SSH connection with the newly added port.
sudo iptables -A INPUT -p tcp --dport 2222 -j ACCEPTOnce you add the firewall rule, you need to reload the firewall to take effect. If You use firewall, you can reload the firewall using the following command.
sudo firewall-cmd --reloadOr if your system use iptables, you can use the following command
sudo service iptables reloadStep 5: Restart the SSH Service
Now that you have configured ssh and added the firewall rule, you need to restart the SSH service to start using the new port for SSH connection. To restart the SSH service, use the following command.
sudo systemctl restart sshStep 6: Testing with SSH Client:
It is a good idea to test a new SSH connection before terminating your SSH connection to the service. Because if you did not do any of the previous steps correctly, there may be a possibility that you will lose your access to the server. I face this problem once. So, before terminating your existing connection, I recommend you test the new port to see if it is working correctly.
One way to test your connection is by using telnet. With telnet, you can check your newly added port. To check your connection with telnet with this command
telnet your-server-ip your-port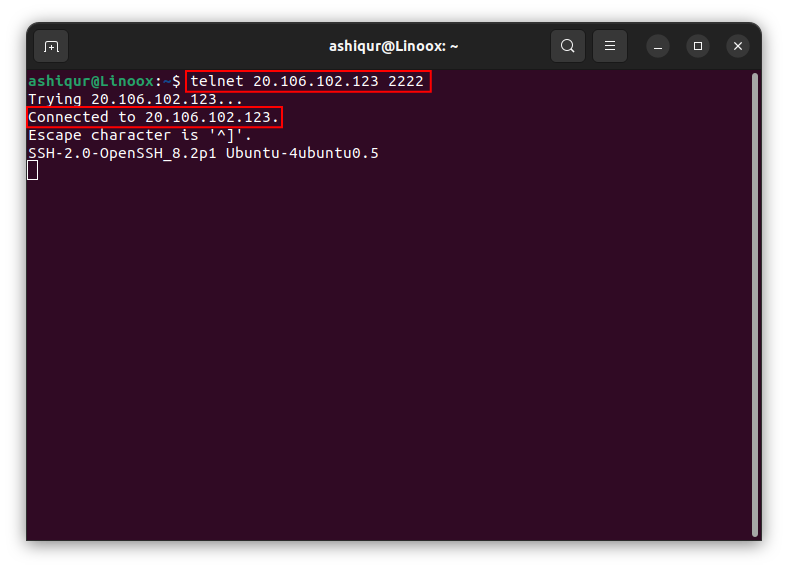
You can also open another window in your terminal and connect to your server with a new port. You can use this command to use a custom port with an SSH connection.
ssh -p port user@host-ip-addressIf you can connect successfully, you have changed your default SSH port to a non-standard one.
Conclusion
Following this step-by-step tutorial, you can change your default SSH port to any custom port. This tutorial applies to most Linux servers such as Debian, Ubuntu, Red Hat Linux Enterprise, CentOS, and other distro with the same architecture as Debian or RHEL.




